ADVISORY SERVICE
IGA Optimization
Unravel a wildly grown environment, redefine structure and regain control.

Identity Governance Administration is becoming more and more crucial
Organizations evolve. There is more digital collaboration with chain partners, and the digital possibilities innovate too. More is possible. As a result, more target groups need to be supported, and the system landscape is constantly renewed. There is a growing need for compliance and protection of (privacy) sensitive data. But the IT environment, business processes and (internal) customer requirements have also become more complex. This organizational growth leads to a recalibration of the facilities and approach. IGA is becoming increasingly important in this regard.
A strong governance foundation
Build a strong governance foundation that enables you to dynamically respond to future developments.
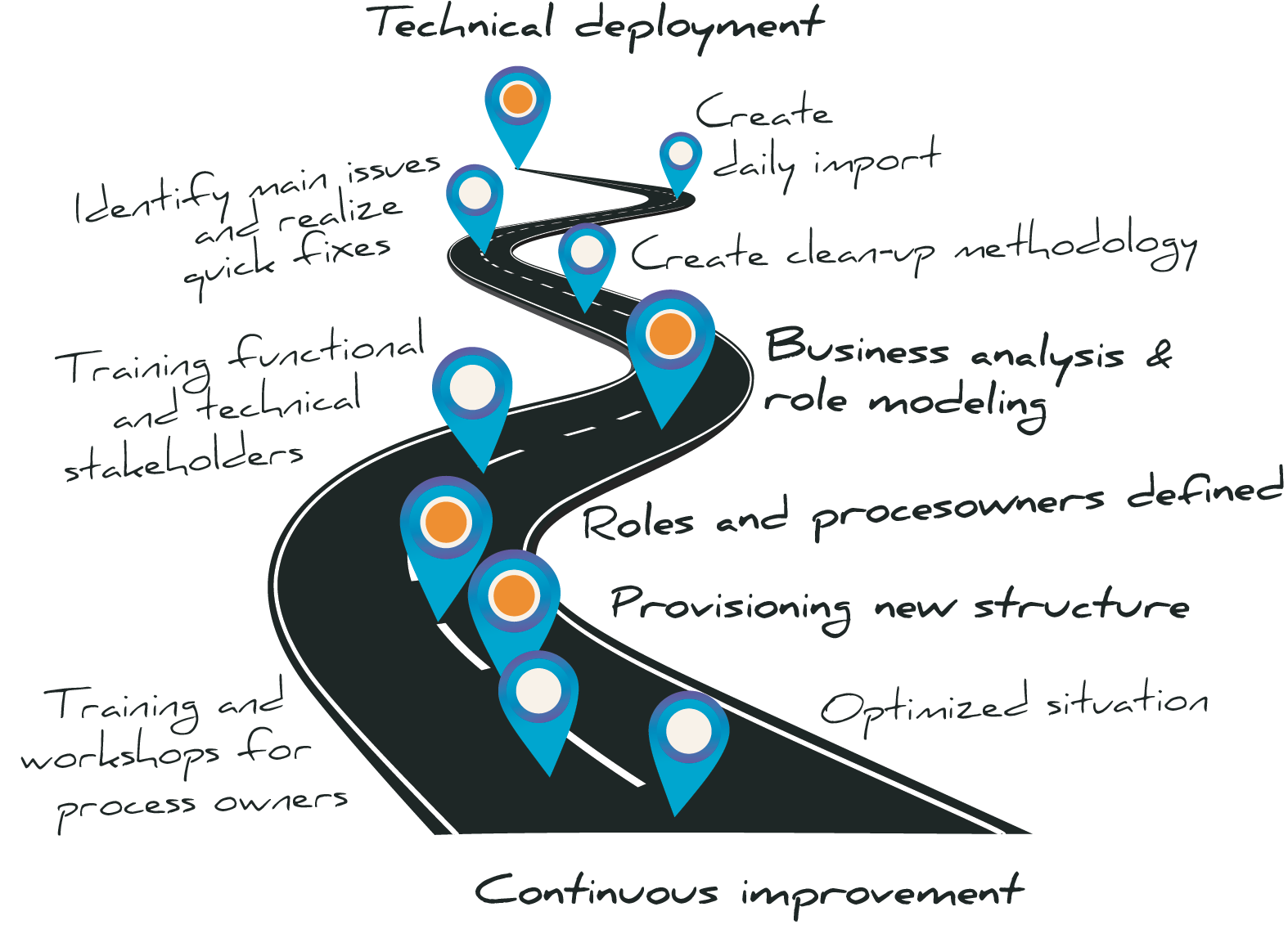
The situation that has arisen over the years has meant that cohesion has been partly lost. If, after the Autorization Analytics, insight has been gained into the current situation, it is time to permanently optimize the situation.
During the IGA Optimization project, the SonicBee team uses the Nexis analysis software to unravel the existing situation. Through discussions between the SonicBee experts and various process owners from the business, an inventory is made of the ideal situation that specifically matches your environment. Various stakeholders are trained. So that the optimized situation lands successfully within the organization. The optimized structure is tested and set up. At the end, you have an optimized situation, supported by the business. You are back in control and remain so thanks to the dynamic IGA environment.
“Deciding which person has what permissions,
and assuring that this permission is justified,
should be a business responsibility.”
Get back in control as a company
SonicBee carries out an IGA Optimization project for you so that cluttered and complex grown environments are cleaned up and improved. This puts you back in control of the optimized IAM environment. The advantages at a glance:
Redefine based on business need!
Optimizing IAM-related business processes based on the requirements of various stakeholders in business operations.
Efficient cleaning
Unraveling complex role structures with role mining.
Careful set-up
Defining access rules based on more extensive Policy Based Access Control (PBAC) capabilities.
Simulate and test
Simulate adapted situations to test the new environment and prevent errors.
Delegate to the business
Outsourcing of processes to business and process owners, such as reporting a new employee (joiner-mover-leaver process).
Achieve compliancy
Easy auditing with an automatic periodic blueprint of the environment.
Related articles